Working in the cloud allows accountants to reduce operating costs and work more efficiently. It allows them to simplify the management of their finances using accounting software and automate administrative functions with software-as-a-service (SaaS)-based applications. However, whilst cloud adoption continues to surge, issues of security and privacy remain a concern for some.
Many still believe that housing data on a physical desktop is safer — but the opposite is true. When using the cloud, your information is securely stored in data centers, managed by service providers who implement advanced security protection at a level which would be extremely complex and expensive for businesses to emulate on premise. The cloud also offers data redundancy, because ultimately, information is stored in multiple locations, allowing for natural disasters or other issues that may disrupt one physical server site.
But users still need to act responsibly and practice safe online behaviors. As accountants handle sensitive data for their customers on a daily basis, they must adopt a risk-averse mindset. A single incident can result in negative consequences for a business, in terms of lost revenue and damage to practice reputation and growth. With that in mind, here are some ways firms can help to protect their data.
Defend against account hijacking
Online criminals target businesses through malicious software, designed to access personal data by infiltrating a user’s PC or mobile device. Web browsers and email filters are fairly successful in filtering out harmful content for us and certain spam messages are easy to spot. However, cyber criminals continue to refine their methods and are getting slicker in their approach.
Some of the more common ways data can be infiltrated is through malware, which typically attacks devices through false links or email attachments. To defend against these types of attacks, businesses should ensure that their network perimeter (e.g., a firewall) is appropriately configured with a unified threat management system, or at least content filtering, and that all forms of remote access are made as secure as possible.
Phishing attacks allow hackers to masquerade as a trusted third party, often in the form of bogus emails in an attempt to extract personal information. Red flags to look out for include generic emails that don't demonstrate they know the receiver, unlikely source email addresses, poor spelling and grammar, or encoded URLs which don’t match the impersonated company. Hackers may request personal information through emails or SMS messages labeled “urgent,” a popular intimidation tactic designed to panic the reader into complying. Genuine service providers will never ask for personal data to be verified in this way.
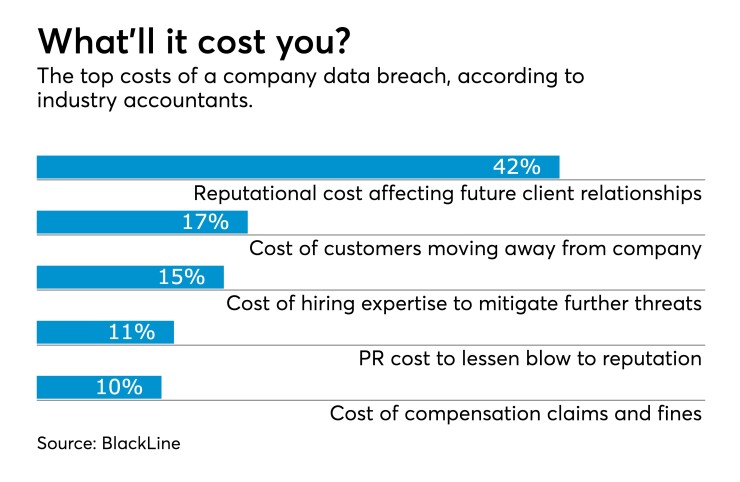
Train your staff
Despite the perception that threats mainly stem from external sources, risks can actually be found much closer to home. It was reportedly the error of a single employee that caused the
In order to address these challenges, practices should set appropriate guidelines as well as upskilling their employees. For instance, running training on common phishing attacks and email scams can dramatically reduce clicks on false links. Monitoring the use of personal mobile devices to access corporate files is also advisable. By taking these types of preventative measures, businesses will ensure their employees are better informed and able to work as a team to tackle external threats.
Take password security seriously
It may seem like there’s a never-ending list of passwords to remember for all of our personal and work-based accounts, and with ever more complex requirements. However, passwords are the first line of defense between our data and third parties, and the stronger and more complex a password is, the better. Advice on this topic has been well publicized, yet surprisingly, some of the most
The best passwords are those which neither people nor computers can guess easily. They should be at least 10 characters and a mixture of numbers, symbols and upper and lowercase letters. It’s recommended to use different passwords for different online accounts, which has enabled password management applications, to become popular. These types of tools allow users to create one master password, automating login on demand and allowing users to share access to subscriptions with others, without revealing actual passwords.
Choose cloud software with care
Increasingly, accounting practices are using automated data capture and workflow management solutions to improve accuracy, reduce costs and speed up back office processes, like those associated with traditional bookkeeping and manual data entry. There is clear business sense in reducing labor spent on unnecessary administration and paperwork and redirecting this resource into more lucrative revenue streams, such as advisory services. And as well as boosting productivity, certain solutions have the convenient side-effect of also improving data protection. However, whether it’s a new accounting software package, or an automated data entry solution, practices should check their solution of choice offers certain security standards before using it. For instance:
- Encryption: This encodes or “scrambles” text, making it indecipherable to non-authorized users and protecting the identifiable information you collect on clients, such as addresses, payroll or tax details. This is a great comfort if a laptop is lost or stolen.
- Two-factor authentication (2FA): When logging into your account, 2FA requires users to verify themselves with a username and/or password, as well as another identifying factor such as a one-time code texted to your cell phone.
- Data replication: This ensures the replicated data can be quickly accessed should the original data be erased by mistake, or via an IT failure or a cyberattack. Specifically, check that your service provider offers point-in-time replication, which takes a snapshot of your data at regular intervals so the most recent version of your files can be restored following an incident.
Don’t become a statistic
Using automated and cloud-based technologies enable firms to cast off outdated and unprofitable practices in the back office. And as we move ahead in this digital age, it will increasingly be the approach forward-thinking accountancy practices adopt.
It will be critical however for these same firms to keep their business secure from threat, deploying solutions which offer robust data protection, user authorization and authentication. As well as driving considerable operational efficiencies for accountants, the right automated solution will efficiently disable security threats and enable businesses to operate with confidence.





