Tax preparers, accountants and auditors working away from their offices as a result of the novel coronavirus pandemic are at risk of falling prey to cybercriminals.
Last month, the IRS issued a warning to taxpayers to beware of scammers calling and emailing them about the stimulus payments from the CARES Act, along with other schemes related to COVID-19, as they could lead to identity theft and tax fraud (see
Dan Blum, a cybersecurity and risk management expert at Security Architects LLC and author of the upcoming book, “
“A lot of it is just the same types of risks that we have had all along,” he said. “We’ve had phishing attacks or exploiting vulnerabilities in internet-facing systems, the use of compromised credentials to break into systems, and the same vulnerabilities and impacts like identity theft. But now we're turning up the volume on all aspects of risk. With the pandemic, companies and government agencies have to go through this forced digitalization.”
He believes the IRS itself is facing some risks with much of its staff now working remotely. “The IRS has enabled its employees to work from home,” said Blum. “In the environment we're in, when you increase the amount of remote access, you have to make some changes to your internal systems and configurations, which can open some gaps for attackers if you haven't executed correctly in how you expand that remote access.”
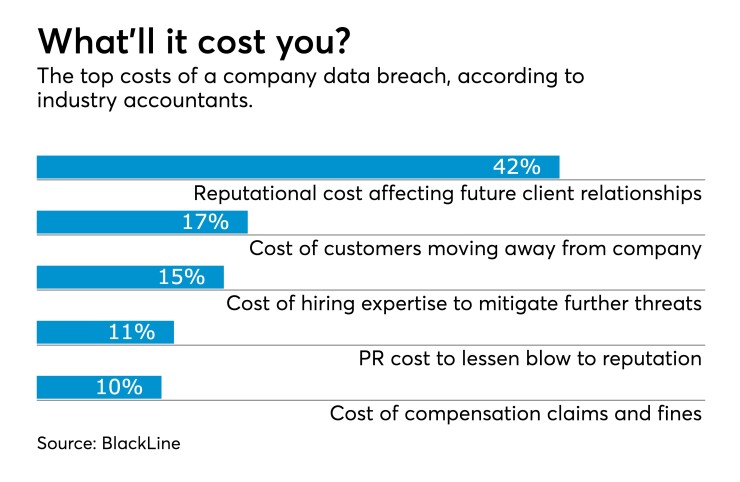
Identity thieves can try to steal the stimulus payments going out to individuals and businesses from the federal government. Accountants need to make sure the money isn’t being stolen from their clients or their own firms.
Sometimes security lapses can be traced to leadership struggles and office politics. “There are a lot of gaps in the management of cybersecurity,” said Blum. “We see all these cybersecurity issues, and they look like technical issues. But really a lot of them are based on leadership issues, and the disconnect between security and business leadership specifically. I was working on technical projects over the years, but so often I'd see company politics or hidden agendas or organizational issues or process issues impeding the success of the technical initiatives, and they impede the success of security operations as well.”
Accounting firms that lower their defenses can become the victims of cyberattacks. One prominent Canadian firm, MNP,
“On one level, accounting firms are like any other business,” said Blum. “They’re either large or midsized or small, but they have the level of security issues that go with that scale of operation. The larger ones are in a better position to deal with the security issues in some respects, particularly if they have a relatively mature security operation. Some of the big ones, like the Big Four, are pretty good because that's part of their business, doing audits and security consulting. But when you get to the smaller ones, we're talking about all the small-business issues, like not enough resources and cybersecurity skills. They’re in the financial services industry, so they're handling funds and the personal data and sensitive financial information of their customers. They are a target-rich environment for financial cybercriminals and for the new crop of ransomware attacks.”
Firms can face risks from insiders as well. Blum knows of a small accounting firm that laid off a vengeful employee last year. “On her way out, she got access to the bank accounts and financial details of 65 of their customers,” he said. “She was just malicious. She changed some passwords, denying services, and the company ended up losing a very promising startup customer. They had to report on this to their customers. They had to disclose it to three state attorneys, and they had several hundred thousand dollars in legal costs."
"But the reason this occurred was because of process issues," he emphasized. "When this woman was let go, they did not terminate her access. All of these customer accounts were being kept in Dropbox folders and files, so they would have had to terminate her access to Dropbox. They also had other other failures here. She didn't even work with all 65 of those customers, and she had a prior identity theft conviction before she worked at the firm, so she never should have been hired in the first place. A bigger company would do background checks, and they would do organized access termination when someone is let go. But the smaller ones are operating in an ad hoc way. They have to trust their employees, and sometimes that trust isn't merited.”
Firms can try to protect themselves from ransomware attacks by doing regular backups, but that’s no guarantee of success, and neither is paying the criminal their ransom.
“The ransomware attackers are basically blackmailers," said Blum. "Often [the data] gets encrypted because that's something they can do in an automated way. They don't even need to look at their work on your accounting firm until their virus reports back to the mothership that, ‘Oh, I got one.’ Then they go look and just wait for the payment. That may be completely automated. But if the attacker is really looking for how they can do the most damage, they could also do things like download your customer database and threaten to dump all the customer names and passwords someplace on the internet publicly. So now, in addition to the loss of availability, you’d have a loss of confidentiality and an actual breach as well as a failure to operate. The other thing the attacker could do is delete things so that even once you restore your backups, things aren't working. It may be that you have a database consistency issue when you restore your backups and it still doesn’t work. There are all kinds of things that can go wrong.”
Doing incremental backups can help, as well as periodically testing the ability to recover the firm’s data from its backup files, which can be useful in the event of any type of disaster, whether it’s ransomware, flood, fire or pandemic.
“You have to test the recovery,” said Blum. “What if we had to restore our database and other systems for any reason? Would they come back online and start working together? Do you have people that know how to fix them? Do you even know the phone number for vendor support to get help with this? Having done that business continuity and disaster recovery testing will help you with the ransomware scenario as well.”
The risks of remote
Now with so many accounting firm staffers working remotely, their processes have changed so much that they may not have access to their offices anymore or the pieces of paper where they wrote down important information. The same goes for their clients.
“There was a day before we knew the tax deadline was being moved, and we were trying to get our taxes done by April 15,” Blum recalled. “On the day when we were supposed to come in for our tax appointment, we actually couldn’t have a physical meeting because of the virus, and we found out from our accountant that Maryland Governor [Larry] Hogan announced a lockdown for the state of Maryland [on March 31]. That included shutting down our accountant’s office building. So on Wednesday he thought that we wouldn't be able to have the appointment and he wouldn't be able to get into his office where all of the records were, and so he couldn’t even do the appointment from his home office. But then it turned out that the governor said tax preparation is an essential business so he could come into his office. He couldn’t have appointments there, but he could come in and get his records. So we were able to do the appointment later, but that’s the kind of thing that’s happening. All the backup stuff and all the disaster recovery stuff may be on paper sitting in a file cabinet someplace and people were just thrown out of their offices.”
Blum believes accounting and financial services firms need to be careful about their cybersecurity at a time like this, when they need to offer remote access to their employees, especially when stay-at-home orders and lockdown orders can be issued with little prior notice.
“When we expand remote access like this, we have to really open up a lot of the layers of defense that used to protect business applications in offices because they used to only be accessible by people that were on their desktop computers on the local area networks, but now they're being accessed remotely,” he said. “So even if you're able to run a VPN, a virtual private network, to get into the office, if you haven’t changed the firewall rules and things like that, this can create a lot of vulnerability if the company didn’t do a proper security assessment of what those vulnerabilities could be and take account of them before the remote access. Of course, nobody had time to do that. The lockdowns were ordered by the governors with days or weeks notice at best.”





